
Last November, the DoD released its updated requirements for the Cybersecurity Maturity Model Certification, dubbed CMMC 2.0. The reason for this update was two-fold: 1) ensuring that government contractors used the practices necessary for protecting sensitive data; and 2) balancing the financial impact of these requirements so that small businesses could afford to implement them. To help streamline this process for certification, the original five levels of CMMC 1.0 were consolidated into three, with updated requirements for each. Read on to learn more about these changes, how they can benefit your team, when they need to be implemented, and how HCRS can help you on your path to certification.
The purpose of CMMC has always been to verify that a government contractor has reached an effective level of cyber resilience. The original five maturity levels were divided into a specific number of practices and processes that were needed to achieve this protection, ranging from basic to advanced. Keep in mind that practices are considered technical activities, while processes are more procedural.
Originally, these levels were only able to be verified by a third-party audit, rather than a contractor’s self-assessment. Now, the Foundational Level of CMMC 2.0 is allowed to be self-assessed because it only applies to contractors that don’t manage Controlled Unclassified Information (CUI) or high value assets (HVA). The chart below from ACQ highlights these changes from CMMC 1.0 to 2.0, including their levels, practice requirements, and assessment options.
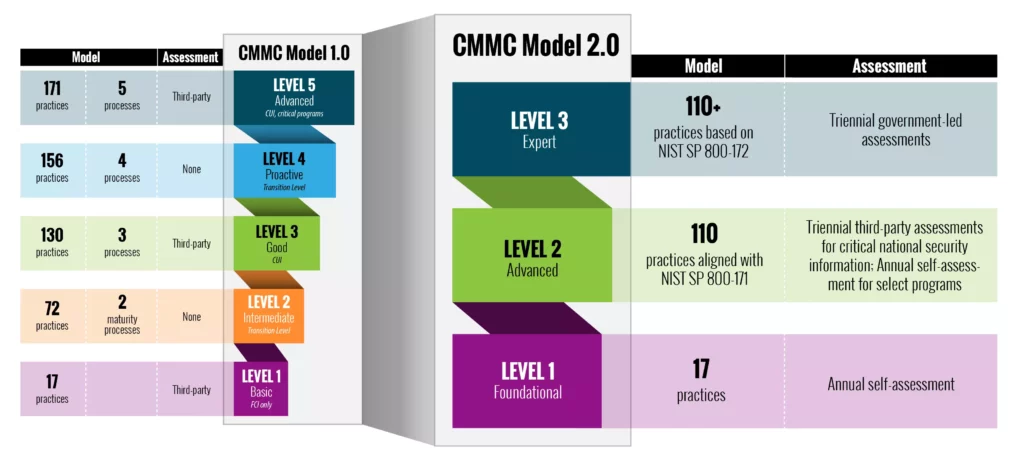
Source: Office of the Under Secretary of Defense. “About CMMC.” www.acq.osd.mil/cmmc/about-us.html
CPO Magazine provides an excellent summary regarding updates to each maturity level. As stated above, Level 1 pertains to those contractors that don’t interact with CUI or HVA. Level 2 contractors deal with CUI but not HVA, and require a third-party assessment only if they deal with CUI considered to be Critical National Security Information. Level 3 is for contractors that use HVA, and their assessments must be performed by the government rather than a C3PAO.
We touched on how the goal of CMMC 2.0 was to allow small businesses the opportunity to obtain certification by implementing changes that were both effective and financially reasonable. This is done primarily through reduced assessments costs.
That said, this revised model is also regarded as a more streamlined approach that aligns with the National Institute of Standards and Technology (NIST), and allows for increased oversight and enforcement of ethical standards.
The DoD still needs to finalize its rulemaking for CMMC 2.0, which means we don’t yet know a firm date on when these changes will need to be implemented. They originally anticipated a completion date within a period of nine to 24 months, which means your team still has plenty of time to identify the areas you need to improve and develop a plan for how to reach them.
HCRS has the ability to guide your team toward CMMC certification by clearly outlining the processes you need for each maturity level. As a Registered Provider Organization (RPO), we don’t perform audits, and we aren’t able to grant this certification for you. But we can share our wealth of government experience and cybersecurity knowledge so that you have the best resources available.
It’s important to note that you can still bid for government contracts while you’re in the process of meeting CMMC certification if you can establish a Plan of Action and Milestones (POA&Ms). This will outline your organization’s known weaknesses and present a strategy on how you intend to correct them.
Even if you aren’t a government contractor, these requirements are relevant. They’re also likely to be adopted across multiple industries in the coming months. It only makes sense to use this framework to develop and enhance your own cyber defense, especially considering the at-risk state of the healthcare sector when it comes to ransomware and other digital threats.
When you’re ready, we’re here to help. Contact us today to schedule time for a needs analysis.








Who We Are
Services
Career Opportunities
Interested in applying for a job with us? HCRS offers competitive compensation and benefits and hires a wide range of professionals. Apply Here

8601 Robert Fulton Drive, Suite 130 | Columbia, Maryland 21046 | Office: (301) 497-1187 Fax: (866) 384-2303
Copyright © 2025 Healthcare Resolution Services, Inc. All rights reserved. | Privacy Policy
