
Cost Drivers, Elements, and Estimated Pricing for CMMC 2.0
Introduction
After a lengthy development period, the proposed rule for CMMC 2.0 was released at the end of 2023. This guide explores the cost drivers and elements of the Department of Defense’s new version, along with real-world examples to help you estimate your expenses for meeting its requirements.
Our goal with sharing this information is twofold: to stress the urgency of these preparations, and to provide realistic expectations for the costs of compliance.
Why Move Forward With CMMC 2.0?
- Compliance Is Fundamental to Your Business Operations
- Noncompliance Puts Your Contracts With the DoD and the VA at Risk
- Compliance Can Be a Time-Consuming and Expensive Process
- Compliance Is Affected by Supply and Demand
- The Number of Cyber AB-Certified Resources Is Limited (Right Now)
Changes to CMMC 2.0: An Overview
For perspective, the main differences present in CMMC 2.0 are:
- Five levels condensed to three.
- Modified totals of maturity processes and practices (or requirements) for each level.
- Restructured types of assessments to achieve each level.
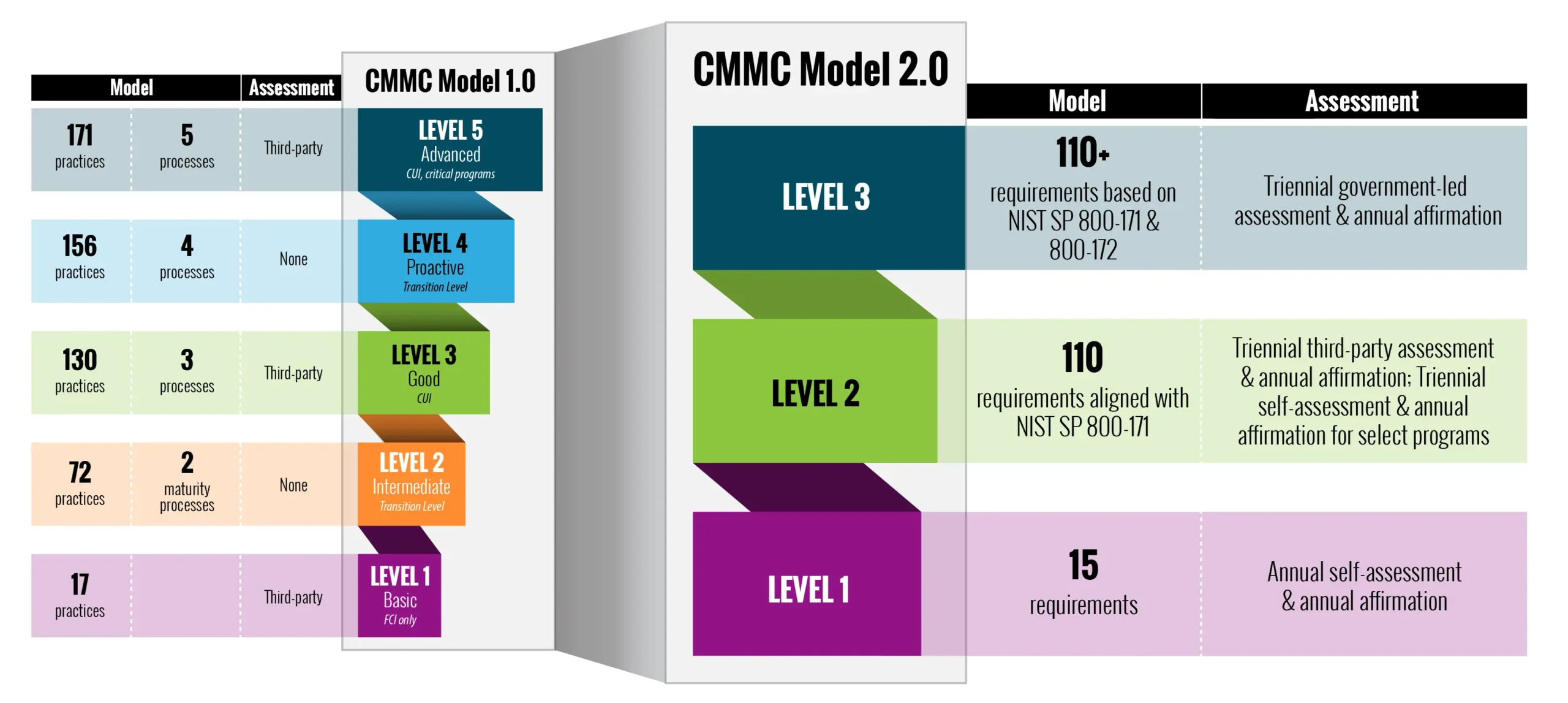
Source: Chief Information Officer, Office of the Department of Defense. ”About CMMC.” dodcio.defense.gov/CMMC/About/
Navigating Compliance Costs
CMMC program requirements are designed to ensure that defense contractors can adequately protect Federal Contract Information (FCI) and Controlled Unclassified Information (CUI). For DoD contractors, the costs from implementing the security requirements under NIST SP 800-171 Rev. 2 should have already been incurred, and are not attributed to this rule. Existing requirements for NIST 800-171 are distinct from costs associated with undergoing a CMMC assessment to verify implementation.
Many organizations underestimate the time and money required to meet CMMC 2.0’s Level 1 and Level 2 requirements. Worse, they often don’t recognize how quickly they can be disqualified from current and future contracts if they fail to produce the appropriate assessment scores and evidence.
The DoD currently has no plans for separate reimbursement of costs to acquire these cybersecurity capabilities. Costs may be recouped via competitively set prices, as companies see fit.
Cost Elements and Drivers
The elements and drivers you can expect to purchase and maintain for certification include:
- Cloud migration.
- Firewalls, routers, switches, and application gateways.
- Multi-factor authentication.
- Hardware, such as computers, printers, laptops, tablets, phones, external disk drives, scanners, copiers, facsimile machines, etc.
- Software purchases and upgrades, such as anti-malware software that detects viruses, worms, Trojan horses, and spyware.
- Security updates, such as patch management, service packs, hot fixes, and antivirus signatures.
- A document management system (DMS) that offers a step-by-step process for completing requirements for NIST SP 800-171 and CMMC 2.0.
- A platform that offers email and file collaboration to protect CUI with end-to-end encryption, and that meets requirements under FedRAMP, FIPS 140-2, and DFARS 7012.
- Dedicated, Cyber AB-approved resources like a Registered Provider Organization (RPO), Registered Practitioner (RP), Certified CMMC Professional (CCP), and Certified CMMC Assessor (CCA).
- Policies, procedures, and checklists.
- An employee badging system.
- Sanitization techniques, such as purging, cryptographic erasure, shredding, and destruction.
- Physical security controls, such as locks, badges, key cards, physical keys, alarm systems, fences, cameras, and guards.
- Ongoing employee awareness and role-based training, recommended quarterly.
- Employee screening and background checks.
- Independent assessments for CMMC 2.0, such as gap analyses, mock audits, reviews by CMMC Third-Party Assessment Organizations (C3PAOs), and remediation.
You can read more about these elements and drivers in this article.
Example Expenses
While specific prices for updating your network may vary, here are some examples* of what you may expect to pay to accommodate them.
| Expenses | Cost |
|---|---|
| Upgraded firewalls, routers, and switches. | $25,000 |
| Telephone system that accommodates FCI and CUI. | $320/month |
| Managed service provider (MSP) that meets FedRAMP, FIPS 140-2, and DFARS 7012 requirements. | $5,000/month |
| Approved document management system (DMS). | $5,000/year |
| Comprehensive testing, cybersecurity simulations, tabletop exercises, and system assessments. | $3,000/year |
| An alarm system and cameras for on-premises defense, with additional protections for 1st floor occupants. | $10,000 installation fee $300/month monitoring expense |
| Cybersecurity insurance. | $3,000/year |
| Cybersecurity policy and procedure development (Level 1). | $2,500 |
| FCI/CUI signage, labels, and marking supplies. | $500 |
| CMMC gap analysis (Level 1). | $5,000 |
| C3PAO assessment (Level 2). | $35,000 |
| Training and conferences. | $25,000/year |
*These prices are meant as an estimate, and can vary based on your business’s specific needs. They represent a small business with 50 active users.
It’s best to speak with a Cyber AB-certified resource — i.e., a CCP or CCA — who can help evaluate the strengths and weaknesses of your current network and provide a more accurate price. They can also establish a timeline for implementing the appropriate changes.
We highly encourage you to take the time now to secure the resources and products you need to drive your business forward. As we get closer to the CMMC 2.0 mandate, you can expect prices to skyrocket — especially with a finite number of resources available.
What You Can Do Now
It may still take several months before a final rule for CMMC is published, followed by an additional 30 days before that rule goes into effect. In other words, it may be summer 2025 before CMMC 2.0 is official — but that doesn’t mean you should be complacent.
CMMC is the enforcement arm for NIST SP 800-171, which is the standard for cybersecurity within the defense industrial base (DIB). If you’ve signed a government contract since 2017, your company has technically acknowledged that it meets all requirements under NIST — and, by extension, CMMC compliance.
Now is the time to identify what requirements you do and don’t meet and create a schedule for completing them. At a minimum, contractors should prepare their information systems for a CMMC assessment (if they have not already), and seriously consider performing a comprehensive self-assessment sooner rather than later. This should include running mock audits and gap analyses, establishing Plans of Action and Milestones (POA&Ms) for the requirements that they lack, obtaining an actual audit from a C3PAO, and submitting audit scores to the Supplier Performance Risk System (SPRS).
Companies that are already required to have NIST 800-171 assessment scores posted in SPRS (based on the requirements in DFARS 252.204-7019 and -7020) should be actively working to remediate any gaps and consider updating their scores to ensure they reflect the current postures of their systems.
With CMMC changes coming sooner than many had anticipated, the DoD has also announced that it will be checking the accuracy of reported scores in SPRS by performing “medium assessments” as described in the DFARS.
While you may choose to do most of your CMMC review and preparation in-house, we highly encourage you to outsource this planning to a battle-tested, Cyber AB-approved resource like Brenda Doles and her team at Healthcare Resolution Services (HCRS).
About Brenda Doles
Mrs. Doles has over 30 years of experience in data management and security within the healthcare and government sectors. She is certified by The Cyber AB (the national accreditation body for CMMC) as a Registered Practitioner and a Certified CMMC Professional. She is also in the process of becoming a Certified CMMC Assessor.
As an active member in the cyber community, Mrs. Doles has met with officials at the White House on multiple occasions to discuss the CMMC ecosystem and its effects on small business contractors.
Contact her today to learn more about a CMMC program for your business.
